Enterprise Secure Access
Zero-Trust Access to Secure Hybrid Network


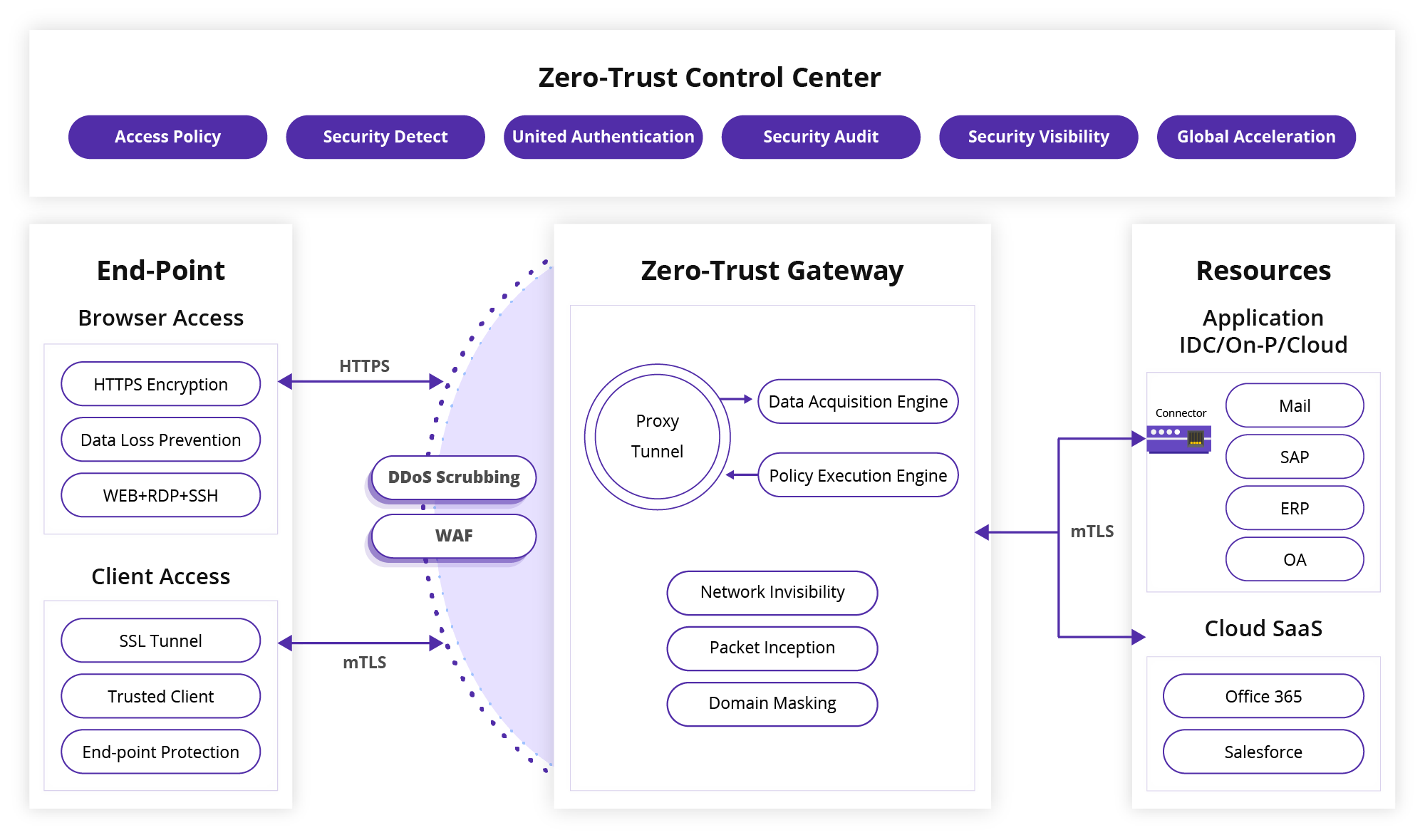
CDNetworks Enterprise Secure Access (ESA) is a cloud service that provides enterprises with secure remote access to applications and data. ESA uses a Zero Trust implementation with a Software-Defined Perimeter(SDP) infrastructure to control access to and from any platform in any environment on any device.
Integrated with identity authentication, application acceleration, and unified management, Enterprise Secure Access ensures that only authorized users can access specific private, public, SaaS applications. In this way, Enterprise Secure Access enables enterprises to establish a security strategy that is safe, efficient, and easy to use in a hybrid networking environment. These tighter security controls also ensure that sensitive data and applications remain private.
Check user identity, device security, and user behavior to ensure that only authorized users and devices are granted access to enterprise applications.
Accelerate remote access and data transmission with a globally distributed DDoS-resistant edge network to provide users with safe and speedy access to applications.
With our Zero Trust security model, you can encrypt data transmission, shield resources behind a security gateway, and protect applications with a cloud-based web application firewall (WAF) to safeguard connections.
Deliver an easy-to-manage platform to set up and maintain applications and users individually and in batches. Provide visualized reports and alerts to aid in intelligent real-time decision-making .
Dynamically adapt granular access control by continuously evaluating user behavior, identification, device security, and threat intelligence to protect enterprise application.
Integrate enterprise, SaaS, multi-cloud, and on-premises applications into one secure and uniform platform. Provides protection regardless of where applications are hosted.
Zero-Trust gateway and control center adds flexibility and accurate access control over employee remote network access. Make work-from-anywhere a reality.
Replace slow, risky, and complex VPNs with a faster, safer, and easy-to-manage solution, reducing costs for facilities, maintenance, and IT human resources.
Network attackers can hack only the applications visible to them. Enterprise Secure Access shields the origin’s IP address and ports behind a security gateway, and intercepts network attacks before they can reach their destination.
Enterprises with branches in multiple regions often have dozens of internal applications, SaaS applications, and IDC/cloud services installed at various locations. A distributed organization relies completely on stable, reliable, and fast connections to support the needs of its remote workforce. As the Internet becomes more vulnerable to cyberattacks, including malware and ransomware attacks, organizations must safeguard themselves from a dynamic, ever-changing attack landscape, while managing employee access privileges to critical and non-critical systems.
Enterprise Secure Access offers:
With the number of remote workers soaring, enterprises with branches and employees distributed in multiple locations use virtual private networks (VPN) to secure business endpoints. VPN lacks granular access management controls, allowing easy exploits via stolen credentials and session hijacking. They are also overly complex, and require IT specialists to perform manual fixes and updates to ensure stable connectivity.
Enterprise Secure Access offers:
Unlike enterprise-hosted systems, SaaS applications such as Salesforce and Office365 and public applications often are hosted in an overseas cloud environment. Such environments are inherently insecure, susceptible to high latency, and predisposed to unstable connections between international networks — all of which lead to a poor user experience that hinders productivity. Most of these apps are hosted on data-sensitive systems that require high-levels of access control.
Enterprise Secure Access offers:
Enterprises with a mobile workforce find their employees accessing internal systems, such as hosted data centers, from any location — home or on the go — using a myriad of devices and carrier networks. These users demand a stable and secure connection to which it is easy to connect.
Enterprise Secure Access offers:
For easy supply chain/retail management, enterprises often need to expose internal supplier and retailing systems to the public network for partners and employees to access. In such scenarios, business systems face unknown security risks from the public network or from malicious users with authorized accounts.
Enterprise Secure Access offers:
A security gateway establishes a secure tunnel between applications and clients to block unauthorized requests from external environments. It also privatizes resource IP addresses and ports to eliminate potential attack surfaces, ensure data integrity, and secure access.
In order to provide you with a more personalized and efficient browsing experience on our websites, we may use cookies and other similar technologies, to collect certain information about you, your preferences and the device you use, as described in CDNetworks Privacy Policy.